Constellation — HTB Sherlock
Medium Sherlock

Medium Sherlock
#Sherlock Scenario
The SOC team has recently been alerted to the potential existence of an insider threat. The suspect employee’s workstation has been secured and examined. During the memory analysis, the Senior DFIR Analyst succeeded in extracting several intriguing URLs from the memory. These are now provided to you for further analysis to uncover any evidence, such as indications of data exfiltration or contact with malicious entities. Should you discover any information regarding the attacking group or individuals involved, you will collaborate closely with the threat intelligence team. Additionally, you will assist the Forensics team in creating a timeline. Warning : This Sherlock will require an element of OSINT and some answers can be found outside of the provided artifacts to complete fully.
Files of this sherlock has two artifacts. Those are,
- IOCs.txt
- NDA_Instructions.pdf
I used two websites for this challenge
Task #1
When did the suspect first start Direct Message (DM) conversations with the external entity (A possible threat actor group which targets organizations by paying employees to leak sensitive data)? (UTC)
first paste the first url in IOCs.txt in unfurl.
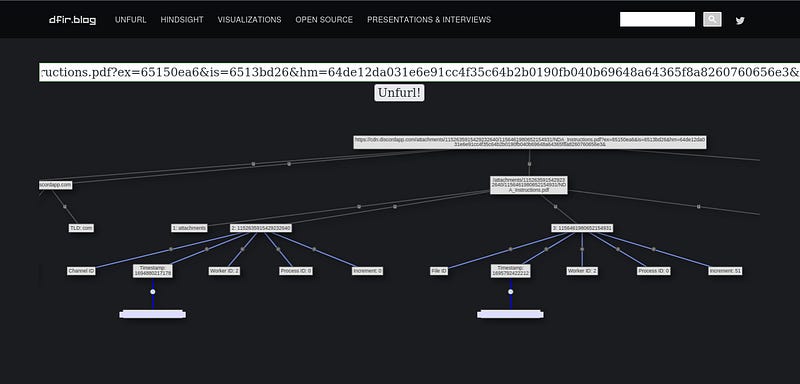
You can find the timestamp there
Task #2
What was the name of the file sent to the suspected insider threat?
Obviously you can find this document in artifact folder
Task #3
When was the file sent to the suspected insider threat? (UTC)
#2nd timestamp in above link pasted in unfurl
Task #4
The suspect utilised Google to search something after receiving the file. What was the search query?
Paste google search url in unfurl
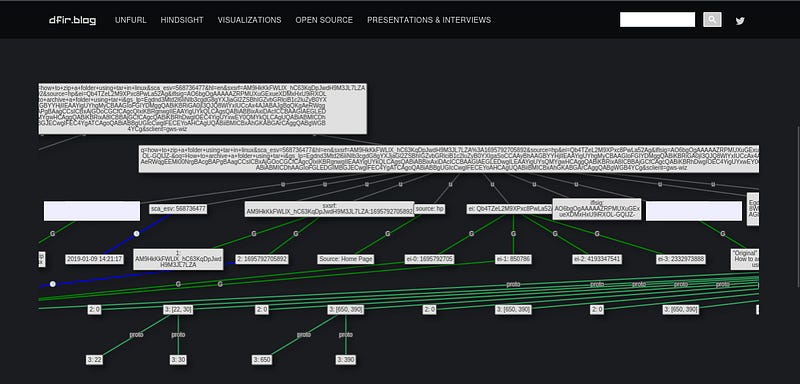
There will be the search query
Task #5 | Task #6
You can find this answer from above website too
Task #7
What is the name of the Hacker group responsible for bribing the insider threat?
Open the pdf artifact file and there will be the threat group name.
Task #8
What is the name of the person suspected of being an Insider Threat?
Open the pdf artifact file and there will be the threat group name.
Task #9
What is the anomalous stated creation date of the file sent to the insider threat? (UTC)
Upload the artifact pdf file to https://exif.tools/ and you can find creation date from there.
Task #10 | Task #11
Make a google search of the email that you found from exif tools web
