Investigating Windows 3.x [TryHackMe] — by BlackFoxK
Find the artifacts resident on the endpoint and sift through captured data to determine what type attack occurred on the endpoint.


Find the artifacts resident on the endpoint and sift through captured data to determine what type attack occurred on the endpoint.
Investigating Windows Room covers many interesting paths in Cyber Security. Such as Sysinternals, Mitre, Event logs, Sysmon and many more. So before begin fire up your hacking machine and connect to Tryhackme VPN Or you can access to attacked windows machine by clicking split screen tab. (if you connecting through vpn you have to connect via RDP connection. Suggest Reminna or freerdp)
Find The Registry key with Encoded Payload
Open autorun log file in the Desktop
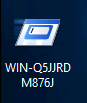
inside log file you can find a suspicious program called Updater
And you can find the registry key from there
What is the registry key with the encoded payload? (full path)
HKCU\Software\Microsoft\*******\**************\*****
Find The Rule Name
Then open the event log file supplied to you
and then click on saved sysmon log
and then click on the first item on the second tab and click on find tab
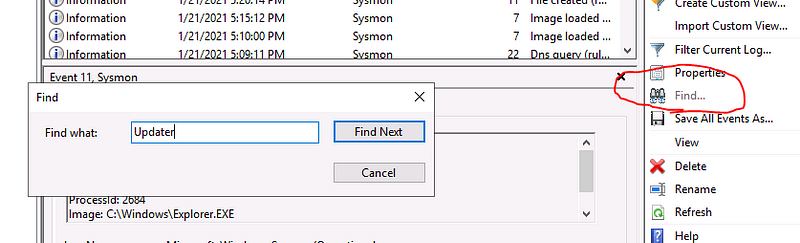
Type “Updater” in the text box and click on find next only one time
Click “cancel” and go to the selected row.
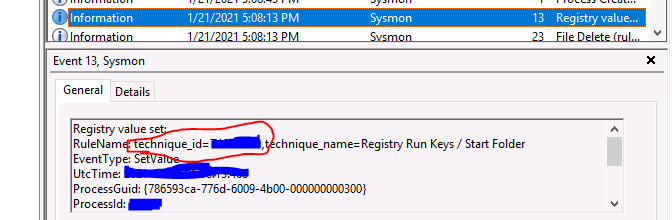
in the “technique_id” field You can find the rule name for this run key generated by Sysmon
What is the rule name for this run key generated by Sysmon?
T****.***
Find the Tactics classified with this MITRE ATT&CK ID
go to this link https://mitre-attack.github.io/attack-navigator/ and search with the id you found
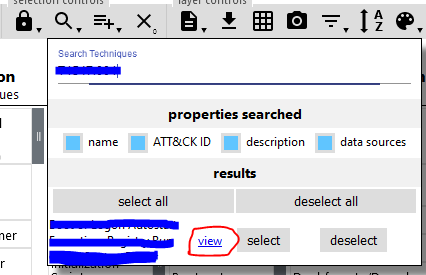
then click on view button
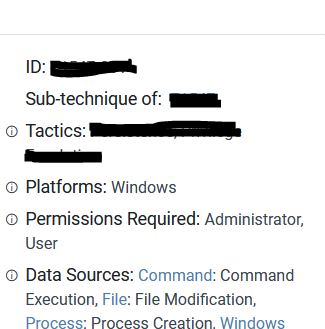
In the Tactics field you can find the answer for third question
What tactics is classified with this MITRE ATT&CK ID?
P**********, ********* **********
Find UTC time for the Sysmon event
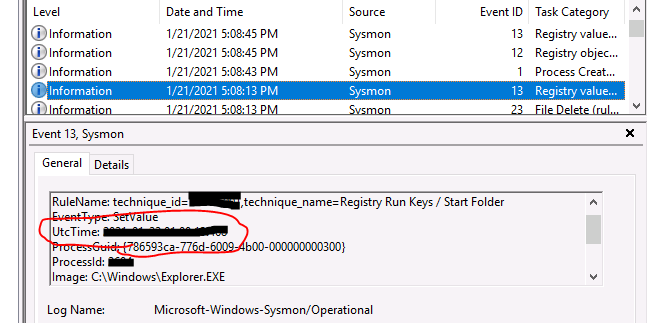
you can find UTC time in here
What was UTC time for the Sysmon event?
2***–**–** **:**:**.***
Find Sysmon Event ID and Event Type
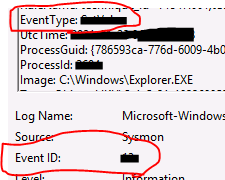
you can find Event id and Event Type in these fields
What was the Sysmon Event ID? Event Type? (answer, answer)
*, S*******
Other Part Will be Continued Soon…..
I’m BlackFoxK